Rooting Android Virtual Device Manager (AVD) for Pentesting
Security testing of mobile applications requires full access to the execution environment, especially when we want to intercept HTTPS traffic with tools like Burp Suite. In this post, I'll show you how to root the Android Studio emulator (AVD) and properly install the Burp certificate. This process is key to performing security analysis and debugging in a controlled environment, without the need to use a physical device.
Opening Virtual Device Manager in Android Studio
Open Virtual Device Manager from Android Studio
Click the + button to add a new virtual device
Select the hardware profile for your virtual device
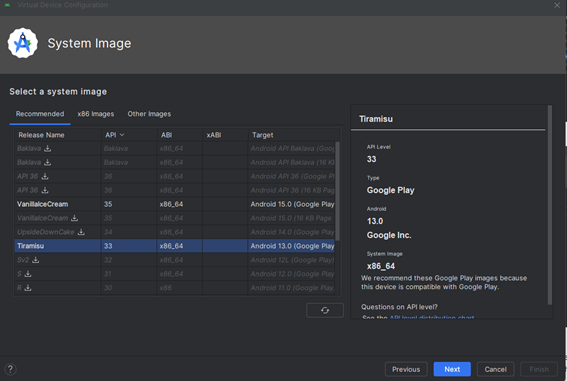
Choose the system image with API level (in this case API 33)

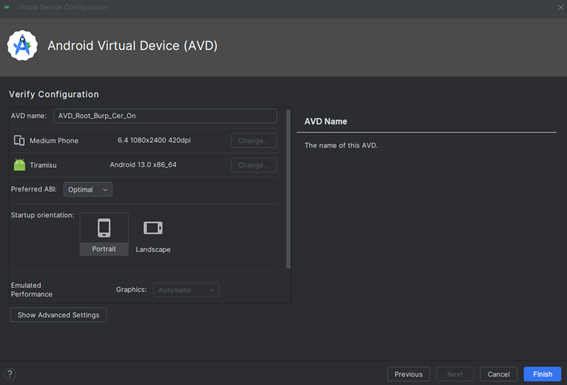
Verify the configuration settings for your AVD

Run ListAllAVDs to find the API version
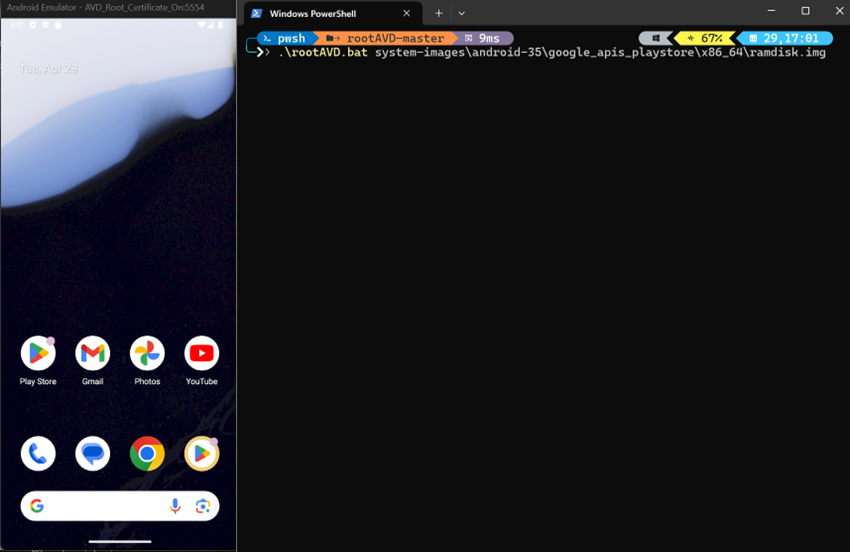
Execute the command to install Magisk on the emulator
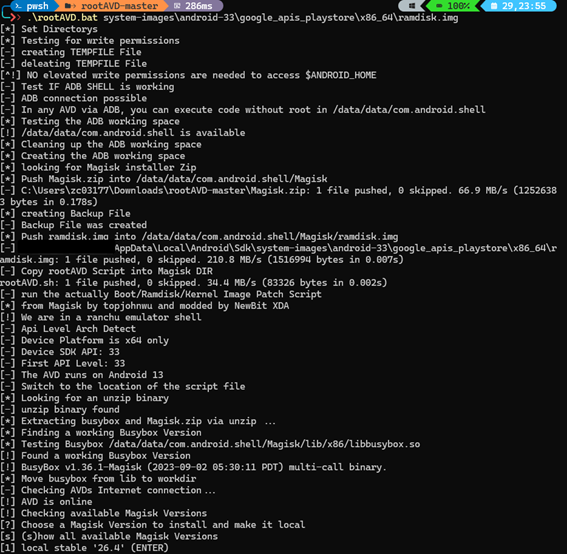
First part of the rootAVD script execution
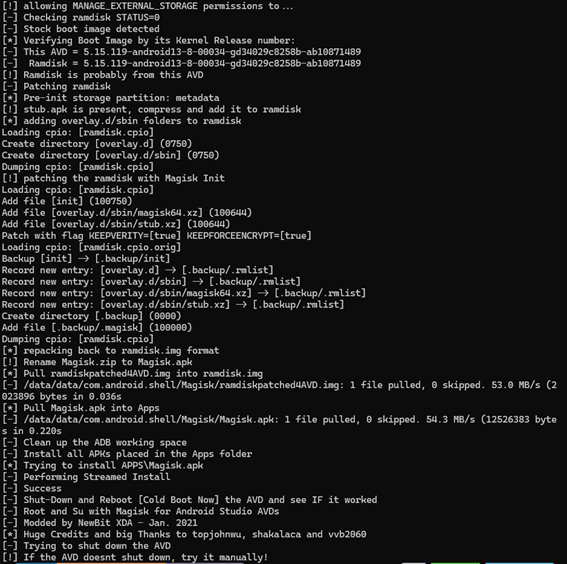
Final part of the rootAVD script execution and patching ramdisk

Android home screen with Magisk app installed
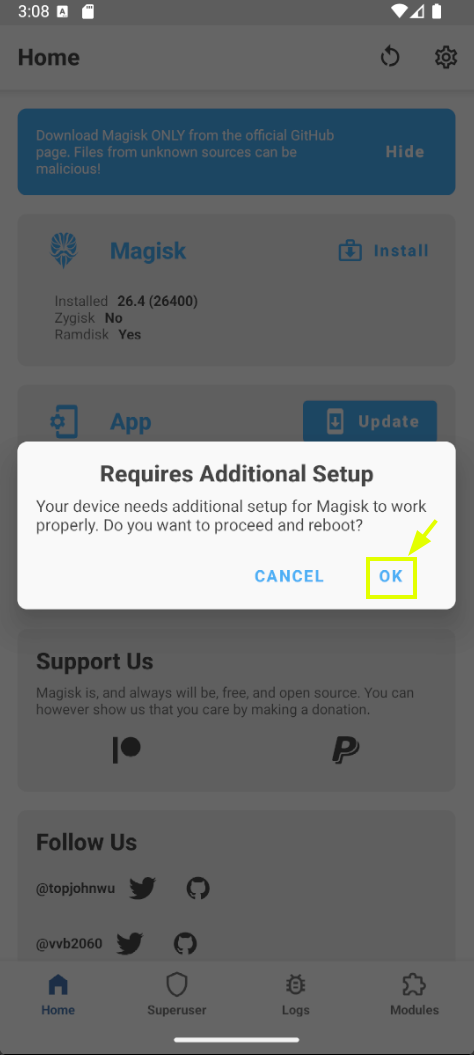
Magisk requires additional setup prompt
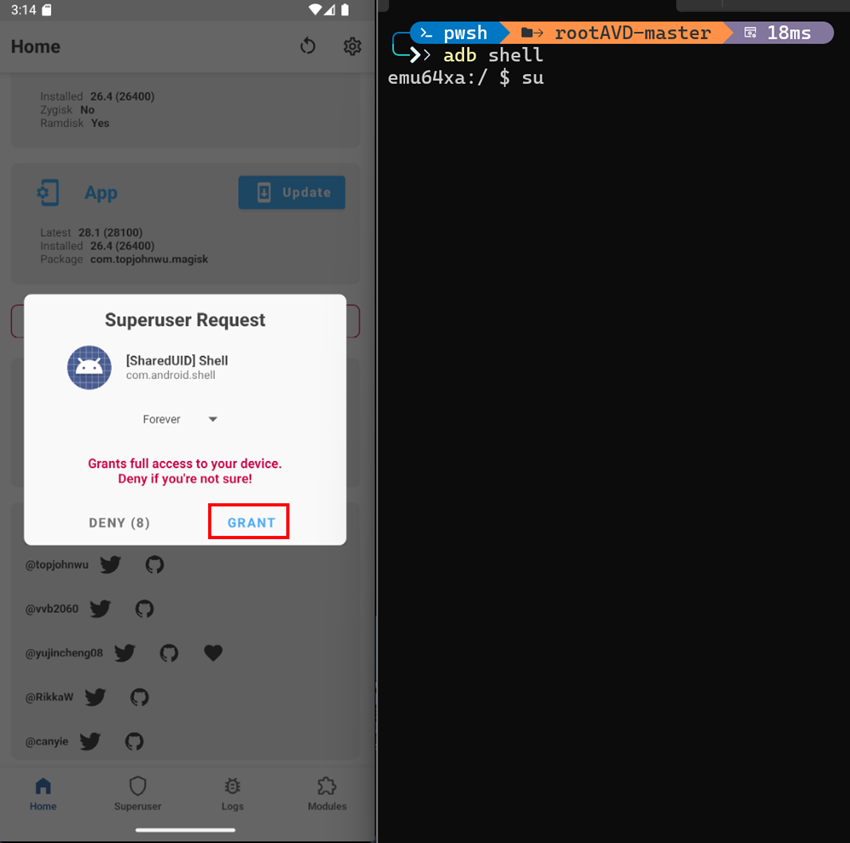
Grant superuser access to shell
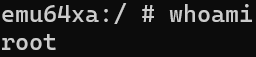
Verifying root access with whoami command
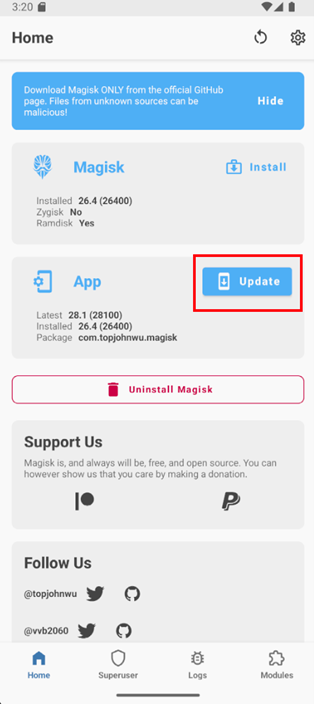
Tap on the Update button in Magisk
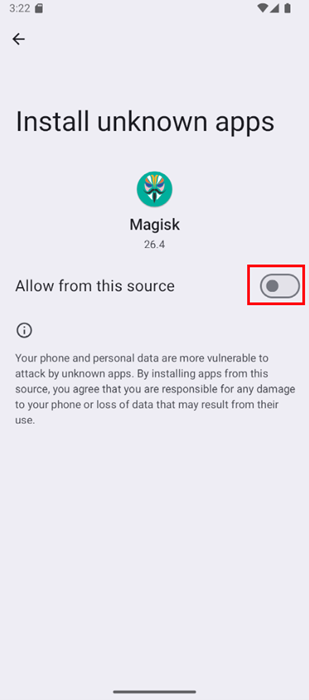
Enable installation from this source
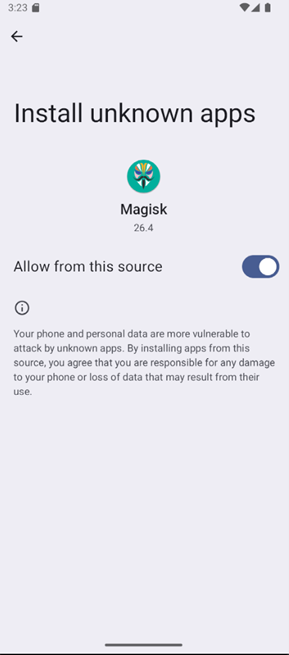
Toggle switched on to allow installation

Install the Magisk update
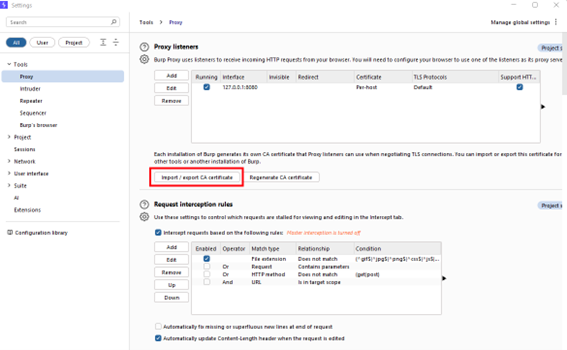
Export the Burp Suite certificate
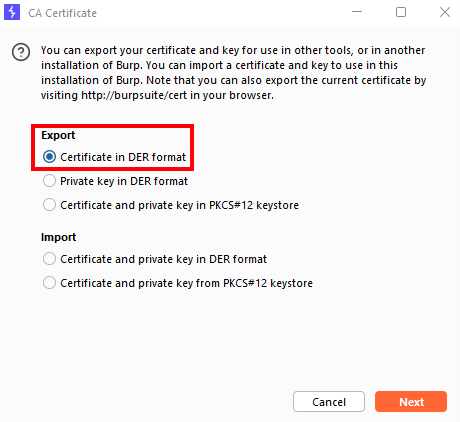
Select Certificate in DER format
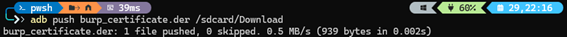
Push the certificate to the device using ADB
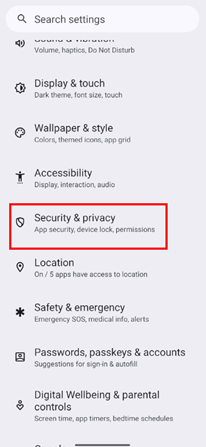
Navigate to Security & privacy in Android settings
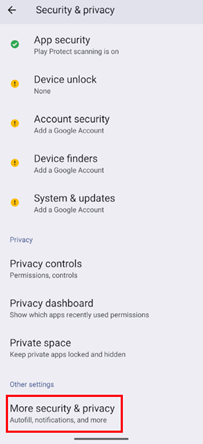
Go to More security & privacy settings
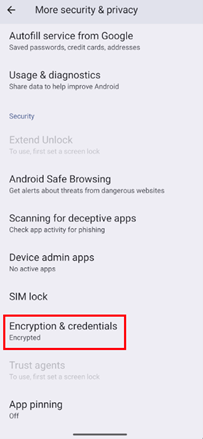
Select Encryption & credentials option
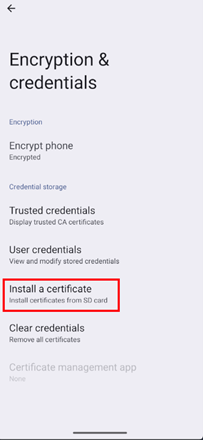
Tap on Install a certificate
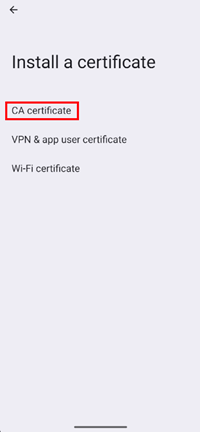
Select CA certificate option
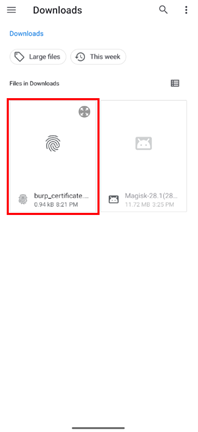
Choose the Burp certificate from Downloads
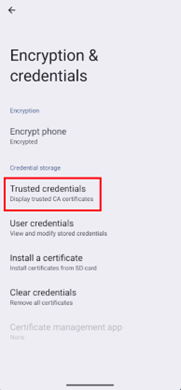
Go to Trusted credentials in the settings
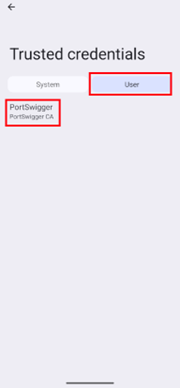
Verify Burp certificate is installed as a trusted certificate
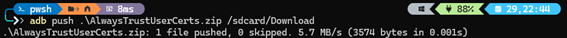
Push the AlwaysTrustUserCerts module to the device
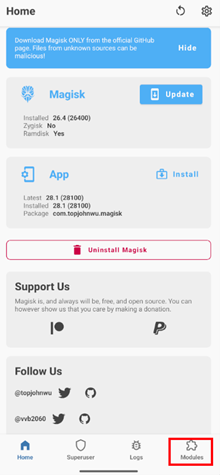
Go to the Modules tab in Magisk

Install from storage option in Magisk
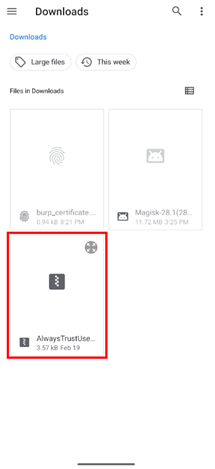
Select AlwaysTrustUserCerts.zip from Downloads
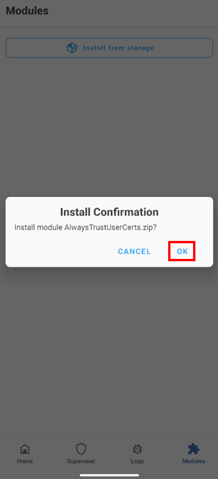
Confirm the installation of the module

Installation in progress for the certificate trust module
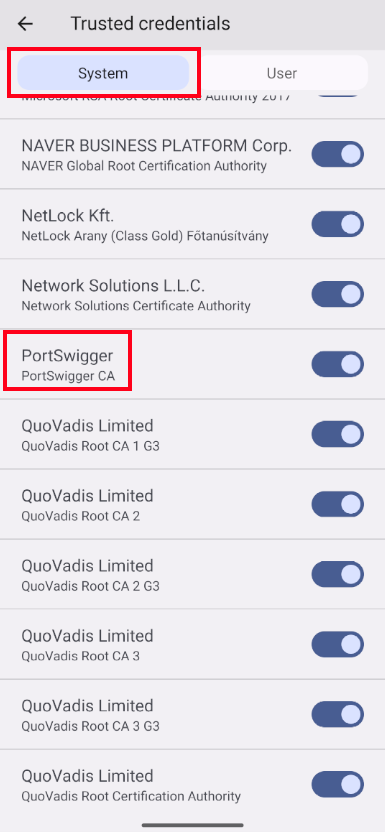
Certificate now installed in the System tab
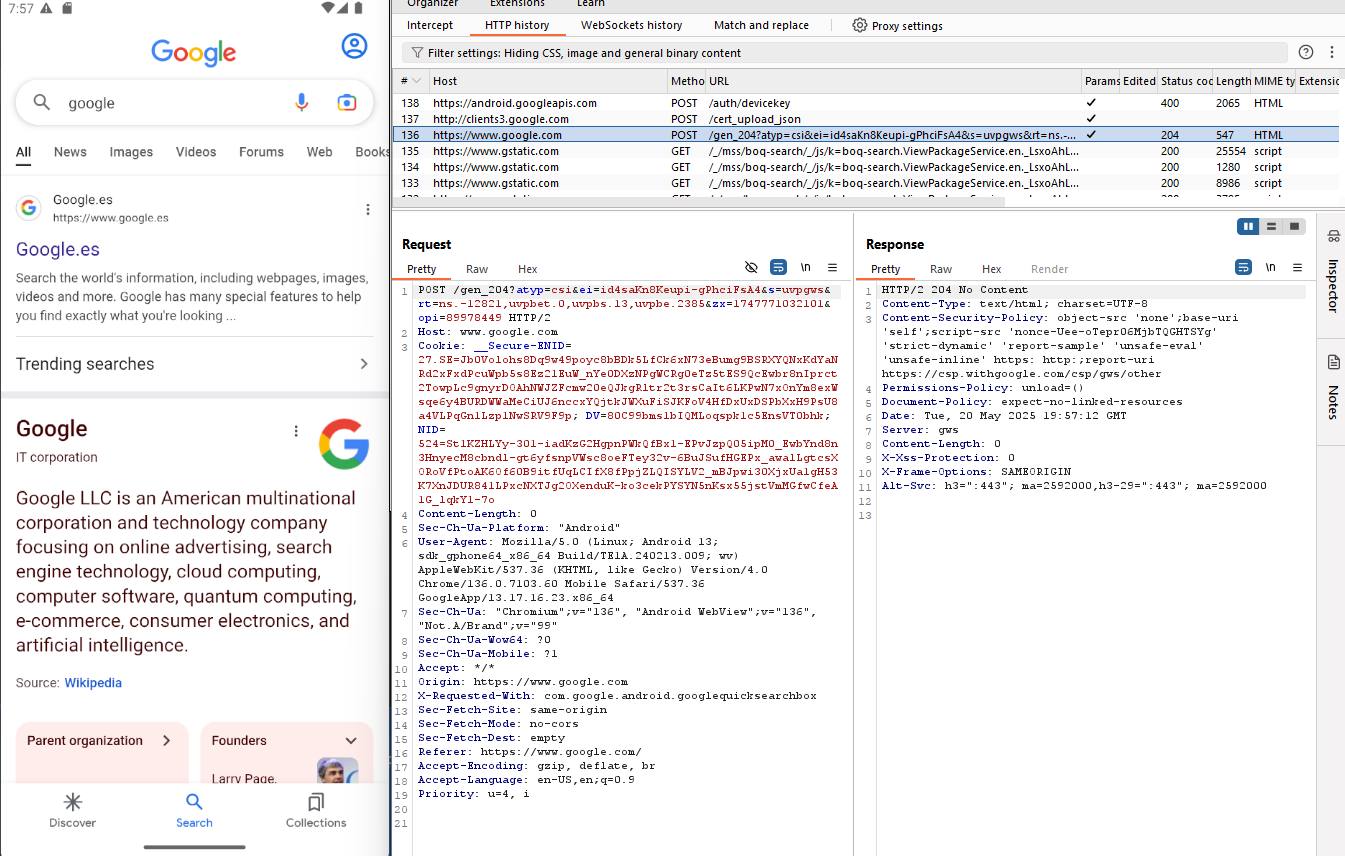
Intercepting HTTPS traffic with Burp Suite
Important Note:
This tutorial is provided for educational and ethical security testing purposes only.

